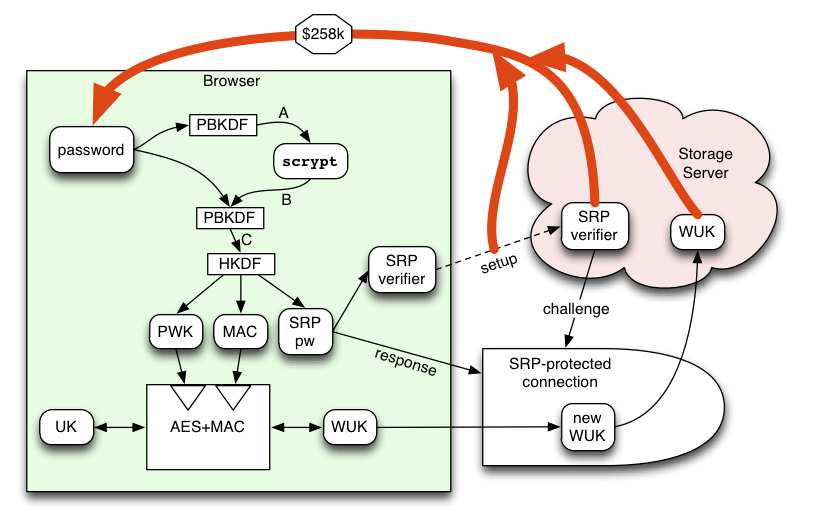
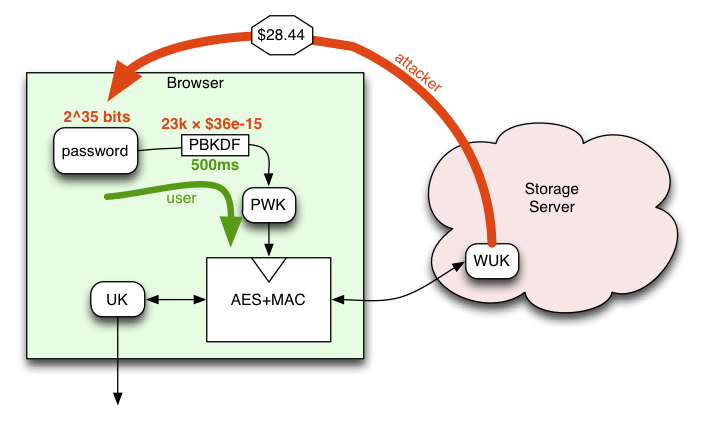
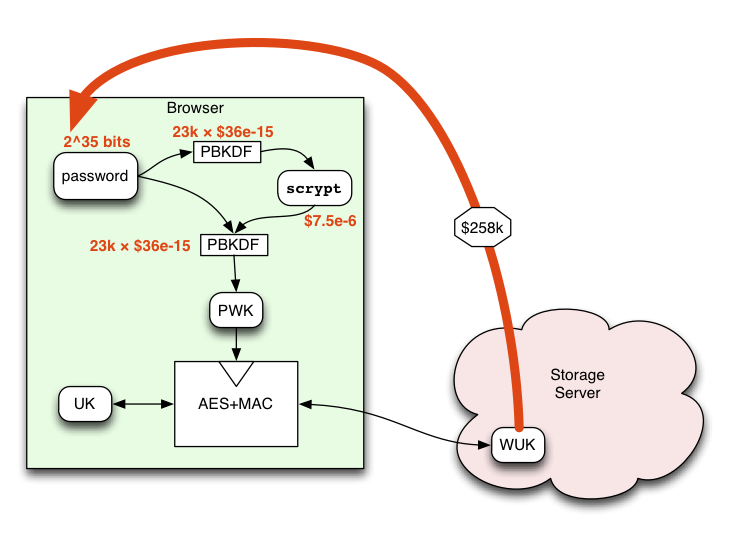
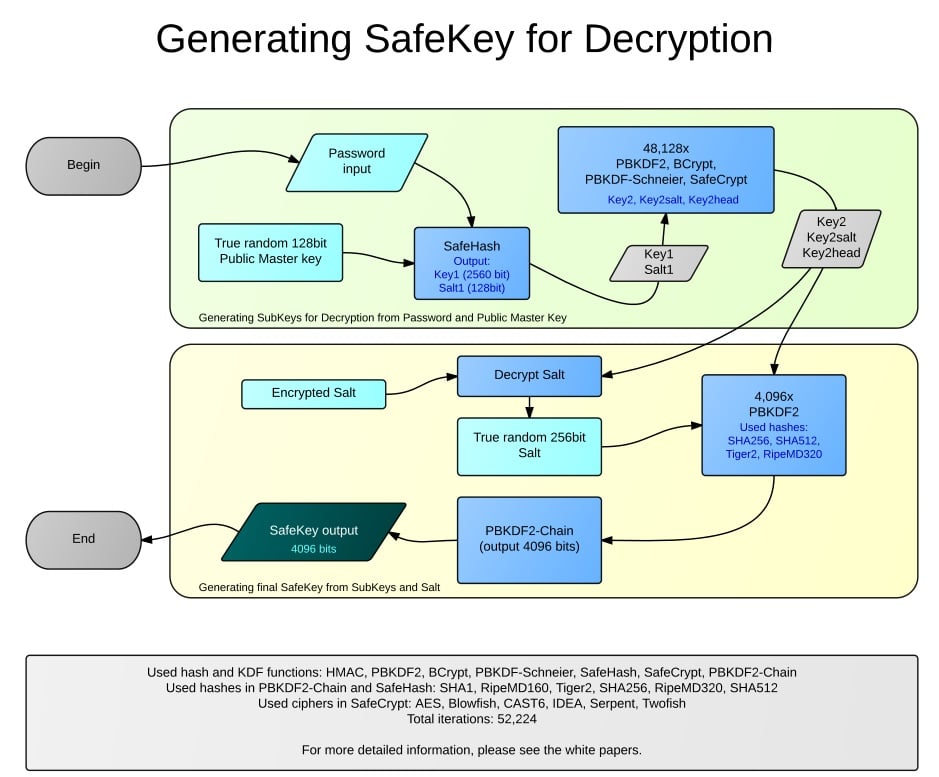
What does PBKDF mean? - Definition of PBKDF - PBKDF stands for Password-Based Key Derivation Function. By AcronymsAndSlang.com

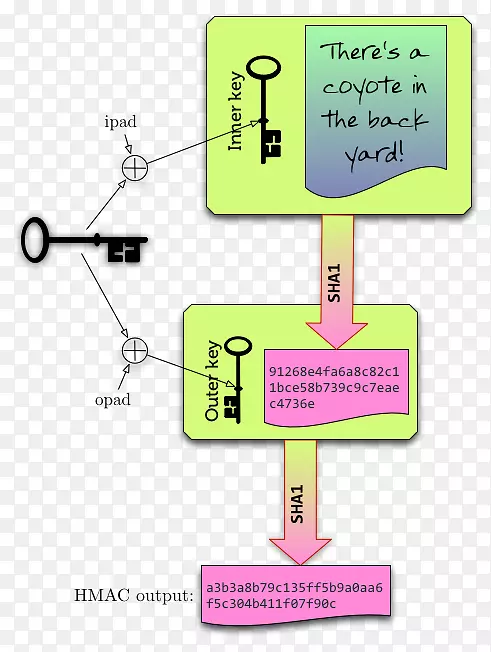
The PBKDF schematic showing the generation of a symmetric key using the... | Download Scientific Diagram
GitHub - peio/PBKDF: Password based key derivation functions (PBKDF1, PBKDF2) as defined in section 5 of PKCS#5

The PBKDF schematic showing the generation of a symmetric key using the... | Download Scientific Diagram
![PDF] SP 800-132. Recommendation for Password-Based Key Derivation: Part 1: Storage Applications | Semantic Scholar PDF] SP 800-132. Recommendation for Password-Based Key Derivation: Part 1: Storage Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/92d0526c772cefb52f5309be4d0efddf7f4497f0/10-Figure1-1.png)
PDF] SP 800-132. Recommendation for Password-Based Key Derivation: Part 1: Storage Applications | Semantic Scholar